2024年12月6日,INFOCOM 2025结果公布,中山大学软件工程学院黄华威研究组(HuangLab)与北航、新加坡科技设计大学、香港浸会大学、新加坡南洋理工大学合作的两篇区块链分片机制的论文被接收。INFOCOM 全称为 IEEE International Conference on Computer Communications, 是CCF-A类计算机网络领域顶会。INFOCOM 2025年的论文接收率为 272/1458 = 18.65%。
两篇被接收论文信息如下。
- [论文1] Jian Zheng (郑简), Huawei Huang* (黄华威,通讯作者), Yinqiu Liu (刘寅秋), Taotao Li (李涛涛), Hong-Ning Dai (戴弘宁), Zibin Zheng (郑子彬), “Justitia: An Incentive Mechanism towards the Fairness of Cross-shard Transactions,” IEEE International Conference on Computer Communications (INFOCOM’25), May 19-22, 2025, London, United Kingdom.
- [论文2] Xinpeng Huang (黄鑫鹏), Wanqing Jie (揭晚晴), Shiwen Zhang (张诗雯), Haofu Yang (杨浩甫), Wangjie Qiu (邱望洁,通讯作者), Qinnan Zhang (张沁楠,通讯作者), Huawei Huang (黄华威), Zehui Xiong (熊泽辉), Shaoting Tang (唐绍婷), Hongwei Zheng (郑宏威), Zhiming Zheng (郑志明), “ContribChain: A Stress-Balanced Blockchain Sharding Protocol with Node Contribution Awareness”, IEEE International Conference on Computer Communications (INFOCOM’25), May 19-22, 2025, London, United Kingdom.
论文下载
通过网盘分享的文件:“INFOCOM25-两篇论文”
链接: https://pan.baidu.com/s/1MAptxA8IRCbTUxCw8Qa4Jw?pwd=uit3
提取码: uit3
两篇论文的背景简介
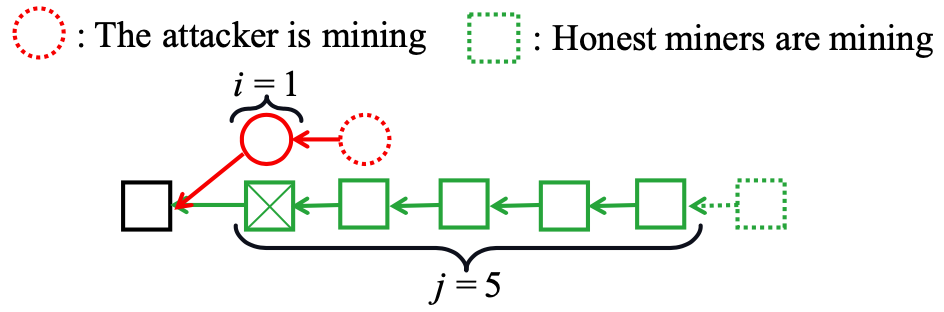
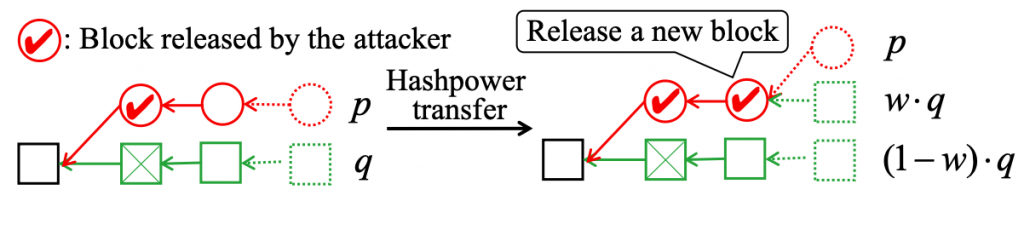
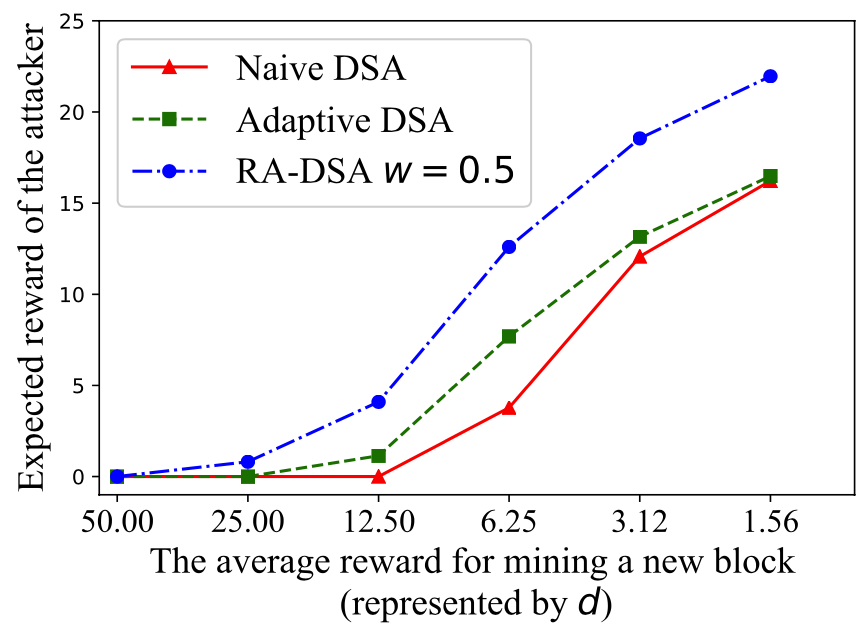
论文1的一作是郑简,中山大学软件工程学院博士一年级同学。郑简同学的研究方向为区块链系统、DeFi 协议设计与经济学分析。自从2020年以本科实习生身份加入 HuangLab 之后,郑简先后参与了 HuangLab 多科研任务,例如参与开发开源区块链实验平台 BlockEmulator (blockemulator.com)、负责研究分片区块链 BrokerChain [INFOCOM 2022] 的分片间交易公平性机制 (即本篇论文提出的方案 Justitia)。此外,郑简同学2021-2022年还研究了针对 PoW (Proof-of-Work) 区块链的自适应新型双花攻击的问题,相关论文“Adaptive double-spending attacks on PoW-based blockchains”发表在TDSC(CCF A类期刊)。
论文2的一作是黄鑫鹏,北航人工智能学院博士一年级同学。黄鑫鹏同学的研究方向为高性能区块链系统、区块链攻击检测。本论文实验平台采用了黄华威研究组开源的区块链实验平台 BlockEmulator,并在此基础上进行ContribChain的系统实现。
论文1的更多背景
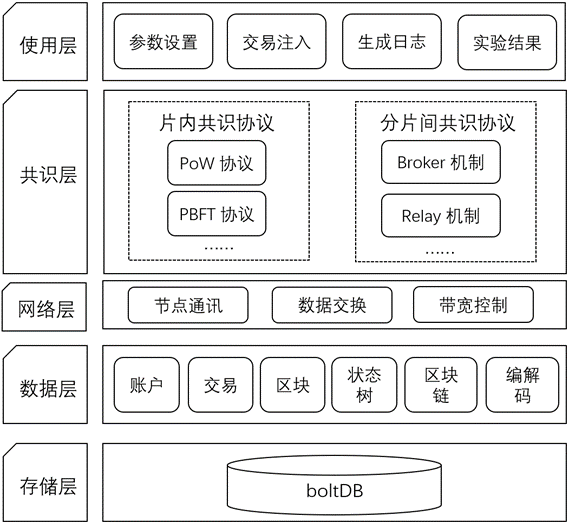
论文1是黄华威研究组自研分片公链BrokerChain (BrokerChain: A Cross-Shard Blockchain Protocol for Account/Balance-based State Sharding, 发表在INFOCOM 2022) 的后续相关工作。BrokerChain现在已经被完善为一个高性能分片区块链基础设施,相关技术方案目前已经支持了华为云区块链、鹏城实验室区块链、上海保交链等企业级区块链系统。2023年5月,研究组将 BrokerChain 的基本实现框架以及研究组后续一系列区块链成果的内置算法、与实验工具集开源为区块链实验平台 BlockEmulator ( blockemulator.com),目前已经得到来自超过80个国家与地区研究者的使用。最近,研究组已经将blockEmulator 技术原理的论文上传到了 arXiv,题目为 “BlockEmulator: An Emulator Enabling to Test Blockchain Sharding Protocols”, 访问链接为 [ https://arxiv.org/abs/2311.03612 ]。在这个文档中,我们详细介绍了 BlockEmulator 的各个重要功能接口,并且展示了 BlockEmulator执行结果的正确性验证的实验。研究组还维护了一个350名的 BlockEmulator 用户群,用于解答使用者遇到的各种技术问题。截止今日,研究组已经使用 BlockEmulator 产出了十余篇区块链论文。欢迎同仁试用 BlockEmulator 来做区块链实验。
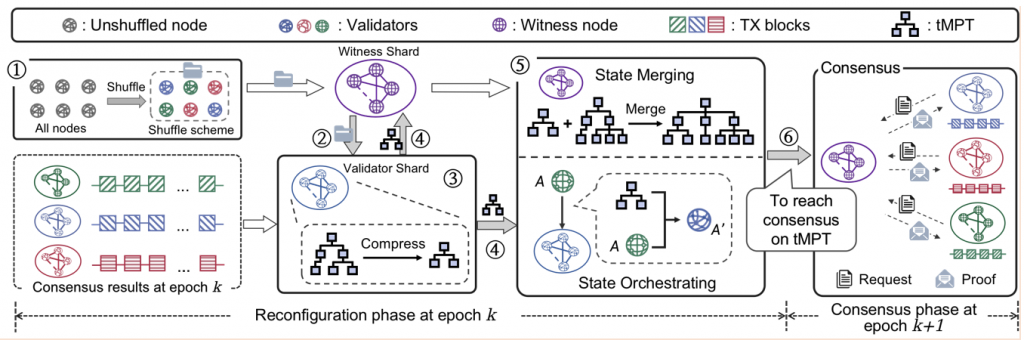
为了帮助读者更清晰地理解跟本次被接收论文1相关的几项工作的关系,这里使用图1来梳理展示。目前,黄华威研究组已经在自研分片区块链 BrokerChain 上基于智能合约开发了一个去中心化金融 (DeFi) 应用 (命名为 BrokerFi;法律法规所限,尚未落地)。如图1所示,BrokerFi 的前端采用研究组自研的 BrokerChain Wallet (BrokerFi 数字钱包);后端即分片区块链BrokerChain;BrokerFi 的核心经济模型是Broker2Earn 协议 [INFOCOM 2024],它展示了一个激励机制,用于帮助 BrokerFi 解决如何招募 Broker 角色参与进 BrokerChain生态的问题。研究组已经毕业的林岳同学设计了 BrokerChain 系统中的账户迁移机制 [INFOCOM 2024]。本次,郑简同学设计的 Justitia 方案针对 BrokerChain 分片区块链中共识协议在验证片内交易 (Intra-shard Transactions, ITXs)与跨分片交易 (Cross-shard Transactions, CTXs)时存在的不公平现象,旨在解决 CTX 因为交易手续费会被拆分给多个分片内的出块者而带来的延迟上链的问题。

两篇论文内容简介
论文1: Justitia: An Incentive Mechanism towards the Fairness of Cross-shard Transactions
一、基本思路
分片区块链技术 (Blockchain Sharding) 是一种确保区块链去中心化特性同时又可以大幅提高区块链性能的可行技术路线。区块链分片的基本思想是将所有区块链节点分成几个分片,每个分片并行处理交易。因此,分片技术可以大大提高区块链网络的吞吐量,并减小交易确认时延。然而,分片技术的引入也带来了新的挑战。首先,在状态分片中(即每个分片维护不同账户的状态),一笔交易涉及到的账户可能在不同的分片中,这种交易通常被称为“跨分片交易(cross-shard transaction, CTX)”,与之相反的是“片内交易(intra-shard transactions, ITX)”。跨分片交易的处理往往比片内交易更加耗时,因此高比例的跨分片交易会对区块链的性能造成巨大负面影响。
BrokerChain [INFOCOM 2022] 分片协议的基本原理是:“做市商账户(broker account)”可以提供通证给分片区块链使用,以此将一笔“跨分片交易”巧妙地化解为两笔容易上链处理的“片内交易”。然而,相对片内交易,跨分片交易(CTXs)会遭遇不公平性现象,而且问题是当前区块链分片技术中的一个普遍存在的挑战。尽管现有解决方案已经解决了CTX的原子性问题,但在处理分片内的交易时,CTXs在交易池内的排队延迟显著高于片内交易(ITXs),这会导致区块链用户的体验变差,并影响分片区块链对 CTXs 的上链公平性。

这里我们使用图2来解释跨分片交易(CTXs)遭遇的不公平性现象。如图2所示,在分片区块链系统底层,一个CTX被解析为两个“纠缠”的子交易,分别在源分片(Source Shard)和目标分片(Destination Shard)内执行共识并上链。当用户提交一笔交易到区块链时,用户并不知道该笔交易是被当做片内交易还是跨分片交易来参与共识。而用户仅仅支付一笔常规的手续费。按照统计规律,该笔交易在一个多分片的区块链系统中大概率会被解析为一个跨分片交易,即CTX。在传统针对 CTX的处理机制中,该笔 CTX涉及的两个子交易需要分别在不同分片(源分片与目标分片)排队等待参与片内共识,原始手续费要被拆分并分别支付给两个分片内的出块者节点。这会导致此CTX在交易池中的排队延迟远高于其他片内交易ITXs,这是因为 ITXs 的手续费并没有被拆分。出块节点会优先打包ITXs。


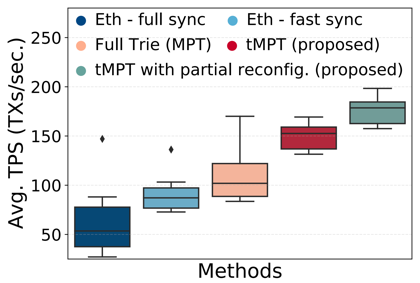
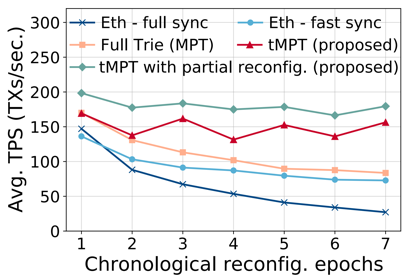
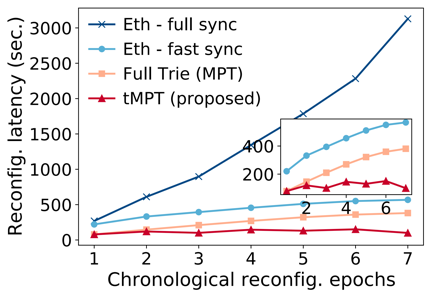
图3和图4的前置实验结果展示了 CTX 会比 ITX 经受更长的交易池内排队时延、更小的上链比例。为了解决CTX遭遇的不公平的问题,我们提出了一种激励机制,命名为Justitia,通过激励区块提议者优先处理CTX,从而减轻它们在交易池中与 ITX 排队延迟的差异。Justitia设计时考虑了分片区块链的基本属性,包括安全性、原子性和公平性。
二、本文贡献
- 协议设计:我们提出一种面了向分片区块链的激励机制Justitia,专注于解决CTX与ITX的公平性问题。机制设计中采用了Shapley值理论,而且确保了多输入多输出(MIMO)类型的CTX的激励公平性。
- 理论保障:我们通过严格的理论分析证明了Justitia机制在分片区块链中能够保证安全性、原子性和公平性,尤其是显著减少了CTX的排队延迟。
- 系统实现:我们在开源分片区块链实验平台BlockEmulator上实现了Justitia机制,并基于以太坊的历史交易数据进行了广泛的性能评估。实验结果表明,Justitia不仅显著降低了CTX的排队延迟,还避免了系统高额补贴导致的经济通胀问题,证明了其面向分片区块链系统的实用性。
论文2:ContribChain: A Stress-Balanced Blockchain Sharding Protocol with Node Contribution Awareness
一、基本思路
区块链分片已成为一种用于提高区块链性能的突出技术,其核心思想是将整个区块链网络划分为多个子网,称为分片。这些分片并行地处理事务,从而提高了区块链的事务吞吐量。此外,分片区块链通过改变每个分片内的节点,对分片进行定期重组,以保证整个区块链网络的安全性。
目前,大量的研究主要集中在降低跨分片交易的比例,实现分片间的负载平衡,以提高分片区块链的性能。通过利用分片技术的并行优势,这些优化方法有助于提高系统吞吐量。但是,现有的方法忽略了分片内的节点组成,而只关注事务层。当分片之间存在性能差异时,即使它们的负载保持平衡,它们的压力也不平衡。
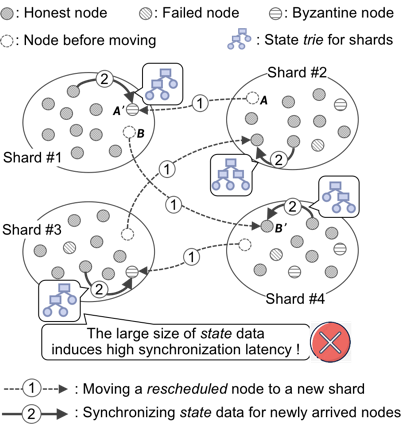
在这里,我们定义分片压力为分片处理事务的能力与工作负载的匹配程度。图5(a)和(b)分别说明了在事务分配和节点分配中不考虑分片性能的影响,事务积压在了处理能力较低的分片中。图5(a)显示了只考虑负载而忽略分片处理能力差异的情形;当前的负载均衡优化和分片重配置的方法侧重于事务分配或节点分配,而忽略了它们的联合影响,这会导致类似图5(b)的情况出现。我们把这个问题定义为当分片事务处理能力和分片负载不匹配时发生的分片间压力不平衡。

为了解决该问题,我们提出了一种新的压力均衡区块链分片协议 ContribChain,并设计了基于节点贡献值的节点分配和账户分配算法,以实现压力均衡。
二、本文贡献
- 压力均衡区块链协议(ContribChain):我们提出动态更新的节点贡献值,以评估节点性能和安全性。此外,账户分配和节点分配算法基于节点和交易水平对分片压力进行评估,确保分片之间的压力平衡。
- 基于节点贡献值的节点分配算法(NACV)和基于性能的账户分配算法(P-Louvain): NACV努力在考虑安全性的情况下,实现已分配节点的性能和分片的负载之间的平衡。P-Louvain将跨分片交易比例最小化,同时确保分片负载和性能相互匹配。
- 系统实现:我们在一个开源的区块链实验平台BlockEmulator上实现了ContribChain。评估结果显示,与最先进的基线相比,P-Louvain分配执行时间减少了86%,跨分片交易比例减少了7.5%;ContribChain提高了35.8%的吞吐量,降低了16%的跨分片交易比例。
团队介绍
黄华威研究组(HuangLab)是中山大学软件工程学院郑子彬院长团队的一个研究组,专注于区块链、Web3、DeFi协议设计等分布式系统协议等领域的研究。团队成员包括副研究员、博士后、硕士和博士研究生,他们在区块链技术的理论和应用方面具有丰富的经验。HuangLab 致力于推动区块链技术的创新和应用,区块链基础设施方面的研究成果广泛发表在顶级期刊和国际会议上,如IEEE/ACM ToN, TPDS, TDSC, INFOCOM、ICDCS、SRDS、IWQoS等,团队成员还出版了《From Blockchain to Web3 & Metaverse》、《Blockchain Scalability》和《从区块链到Web3: 构建未来互联网生态》等区块链相关书籍。
黄华威研究组学术主页:http://xintelligence.pro
HuangLab 开发了BlockEmulator,这是一个区块链实验工具,用于验证新的协议和机制,特别是区块链分片协议。该工具支持以太坊历史交易的回放,能自动输出实验日志文件,帮助研究人员方便地收集实验数据并绘制实验图表。BlockEmulator以Go语言实现,支持定制化开发,适用于轻量级区块链系统的实验平台搭建。
BlockEmulator 主页:blockemulator.com
黄华威研究组微信公众号:Huang-Lab